WP6-01: Difference between revisions
Jump to navigation
Jump to search
| Line 1: | Line 1: | ||
= | = Asset driven Cybersecurity Workflow = | ||
{|class="wikitable" | {|class="wikitable" | ||
| ID|| WP6-01 | | ID|| WP6-01 | ||
| Line 7: | Line 7: | ||
| Levels || Tool | | Levels || Tool | ||
|- | |- | ||
| Require || Windows, | | Require || Windows, [https://c4d.lias-lab.fr/index.php/WP6-02 AIT Security Analysis Tool] | ||
|- | |- | ||
| Provide ||Asset driven cybersecurity workflow. | | Provide || Asset driven cybersecurity workflow. | ||
|} | |} | ||
== Detailed Description == | == Detailed Description == | ||
An asset-driven analysis approach was introduced in the AIT Security Analysis Tool, the figure below shows the resulting cybersecurity workflow. | |||
[[File:AIT_asset_workflow.png|600px|thumb|frame|center| Asset driven Cybersecurity Workflow]] | |||
== Interoperability with other C4D tools == | == Interoperability with other C4D tools == | ||
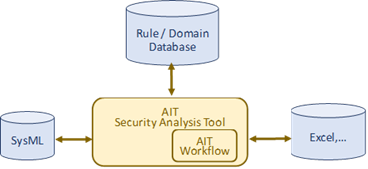
The Asset driven Cybersecurity Workflow as part of the [https://c4d.lias-lab.fr/index.php/WP6-02 AIT Security Analysis Tool] offers extended analysis options for the SysML models. | |||
[[File:AIT_TG_toolchain.png|600px|thumb|frame|center| AIT Security Analysis Tool Toolchain]] | |||
Latest revision as of 13:22, 10 October 2022
Asset driven Cybersecurity Workflow
| ID | WP6-01 |
| Contributor | AIT |
| Levels | Tool |
| Require | Windows, AIT Security Analysis Tool |
| Provide | Asset driven cybersecurity workflow. |
Detailed Description
An asset-driven analysis approach was introduced in the AIT Security Analysis Tool, the figure below shows the resulting cybersecurity workflow.
Interoperability with other C4D tools
The Asset driven Cybersecurity Workflow as part of the AIT Security Analysis Tool offers extended analysis options for the SysML models.