WP6-02
ThreatGet – Post- / Precondition
| ID | WP6-02 |
| Contributor | AIT |
| Levels | Tool |
| Require | Windows, Enterprise Architect, SysML model |
| Provide | Threat Analysis and Risk Management. |
| Input | SysML model |
| Output | Threat Analysis and Risk Assesment, Report |
| C4D tooling | n.a. |
| TRL | 4 (for application to Drone Systems) |
| License | Commercial, Non-Commercial, Academic |
| URL | https://www.threatget.com/ |
ThreatGet offers an automated security (threat) analysis and supports risk managements. This is based on a model of the system and a database of relevant threats, weaknesses and vulnerabilities. The system model is analyzed, potential threats are identified and guidance for threat treatment is provided. For certification the tool offers a report function.
Detailed Description
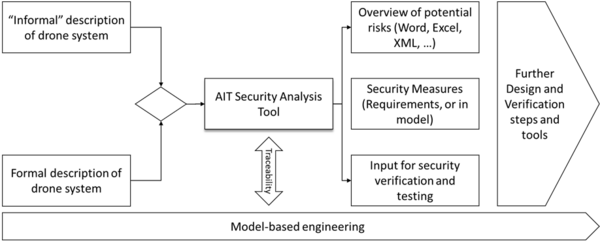
The AIT Security Analysis Tool can be used as analysis tool to identify security issues in a design and verification toolchain and also to provide input for security testing and analysis. An overview of interactions is shown in in the following figure.
The model in the tool can be based either on a informal description of a system (e.g. developed from scratch) or based on an already existing system model (e.g. formal description). In the case of a formal description there is the potential to ensure traceability between the existing model and the model for the security analysis. Outcome of the analysis are:
- A list of potential risks and attacks, where likelihood and impact can be rated to enable risk assessment.
- Based on the risks, security measures can be assigned and used as input for further design and development. Either the security measures can be directly defined in the model, or a requirement document can be defined.
- Identified risks and attacks can also be used as input for security testing and verification.
Contribution and Improvements
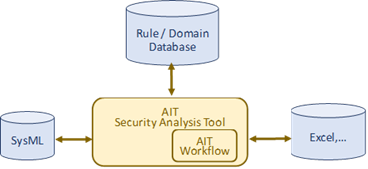
In context of Comp4Drones ThreatGet focuses on an analysis of potential drone usage scenarios and architectures to identify potential security risks and evaluate mitigation measures. For this AIT developed a drone-specific Toolbox. The Toolbox consists of a set of Drone and UAV-domain specific elements, which are divided into generic elements and more specific sub-elements as shown in the following figure.
Interoperability with other C4D tools
While the AIT Security Analysis utilizes an enhanced Dataflow Diagram / Architecture Model for the threat analysis, there is a possibility to connect this model with traces to an SysML Model and interact with other SysML based Tools. In addition to that risk identified and requirements defined can be exchanged with requirement management tools, e.g. Excel, XML, RIF/ReqIF. An asset driven Cybersecurity Workflow AIT Workflow was developed for extended analysis options for the system models.